Further Thoughts on Stealth AirTags

Updated 2025/01/12: Added go-haystack link and AirTag + IMU Proof of Concept
In 2022, I spent a week working with a small team analyzing how Bluetooth item trackers (eg: Apple AirTags, Tile) can be covertly used for malicious purposes, and developing processes and tools to detect them, as a part of GeekWeek 7.5, the Canadian Centre for Cyber Security’s (CCCS) annual cybersecurity workshop. I wrote about my experience here: /exploring-bluetooth-trackers-at-geekweek-7-5/.
Stolen Car Experience
I’ve revisited this experience a few times - once, earlier this year, when one of my friends shared his brother’s experience with car theft. The victim attempted to locate the car using the AirTag he’d hidden in the spare tire compartment, but apparently the thieves had detected and removed the device.
Stealth Air Tags
Tracking a stolen car seemed like an potentially interesting application for a clone ‘Stealth’ AirTag, which consists of small tweaks built on the work of SEEMOO Lab’s Open Haystack. The Stealth AirTag we built evaded detection by altering the AirTag clone’s keys and transmit power at random intervals. It could be further improved with the addition of an IMU (inertial measurement unit), such that it only broadcasts when it is on the move, making it incredibly tricky to find. For most people, a cloned AirTag is not very practical - the Open Haystack application required a Mac, and the setup required to connect it to the Apple Find My network wasn’t straightforward.
New Open Source FindMy Projects
I was thinking about this again recently when I came across the following projects:
- A collection of Python FindMy code: Everything you need to query Apple’s FindMy network!
- Track personal Bluetooth devices via Apple’s “Find My” network using OpenHaystack and Macless-Haystack with tools written in Go/TinyGo
I could envision low-volume custom AirTag clones, that would only broadcast their position when the IMU detected it was moving. The way Find My has been developed, I think it would be challenging for Apple to block these devices from leveraging its Find My network. This Python library would facilitate building a client side app, which could be packaged with the clone AirTag, and work around the challenges I had with the Open Haystack application. This would probably fall well outside of Apple’s Terms of Service - presumably if a market developed for clone devices, they could find a way to block access to non-official clients and modify their devices to avoid relaying the position of clone AirTags.
Digital Camouflage
Another solution would be to modify a genuine AirTag, to selectively turn it on and off. Envision a device similar to Elevation Lab’s TimeCapsule - 10-Year AirTag Battery.

To the Elevation Lab product, add a microcontroller and an IMU, which would control power to the AirTag.
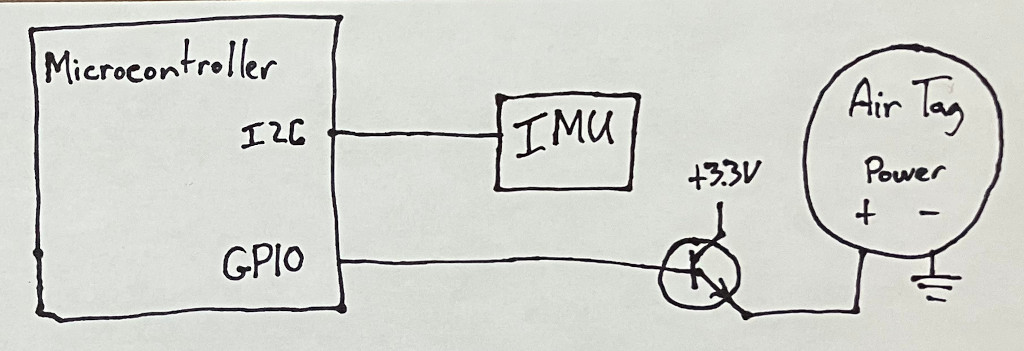
If no movement is detected, the AirTag remains un-powered and does not broadcast. When movement is detected, power the AirTag, and start broadcasting. As the design is an accessory to a genuine AirTag, it remains usable with Apple’s software and devices. Power could be controlled to the AirTag in such a way to not trigger the tracking notification on nearby phones. A device could even be built to support multiple AirTags, and cycle power to each of them - this would have a similar impact to changing the keys seen on some clone Stealth AirTags. It’s like adding digital camouflage to an AirTag!
Proof of Concept
Although the idea was straightforward, and I had no need for such a device, I had all the parts, so I set about building a proof of concept, where the power was selectively supplied to an AirTag, based on a motion-driven algorithm running on an external microcontroller. Genuine AirTags now cost CAD$39, and I was a bit hesitant to solder leads on one of my AirTags. So I built a “dummy” CR2032 cell with power leads using two pennies (out of circulation in Canada since 2013!).
And - the AirTag wouldn’t power up with my dummy cell. I had previously found the Apple AirTag super sensitive to the batteries it accepts - I replaced the stock battery with Duracell CR2032s and it wouldn’t work - Duracell batteries have a bitter coating to discourage small children from swallowing them - I had to sand off the coating before the AirTag would power up.
So I decided to build my proof of concept with an AirTag clone - a “Loshall” tag compatible with Apple Find My. Note that the AliExpress listing indicates it is a Xiaomi product - it is not, but it did work with Apple Find My. I connected it to a circuit with an ESP32 microcontroller, an MPU-6050 IMU, a 2N2222 transistor, and an LED to indicate when power is being supplied to the AirTag.
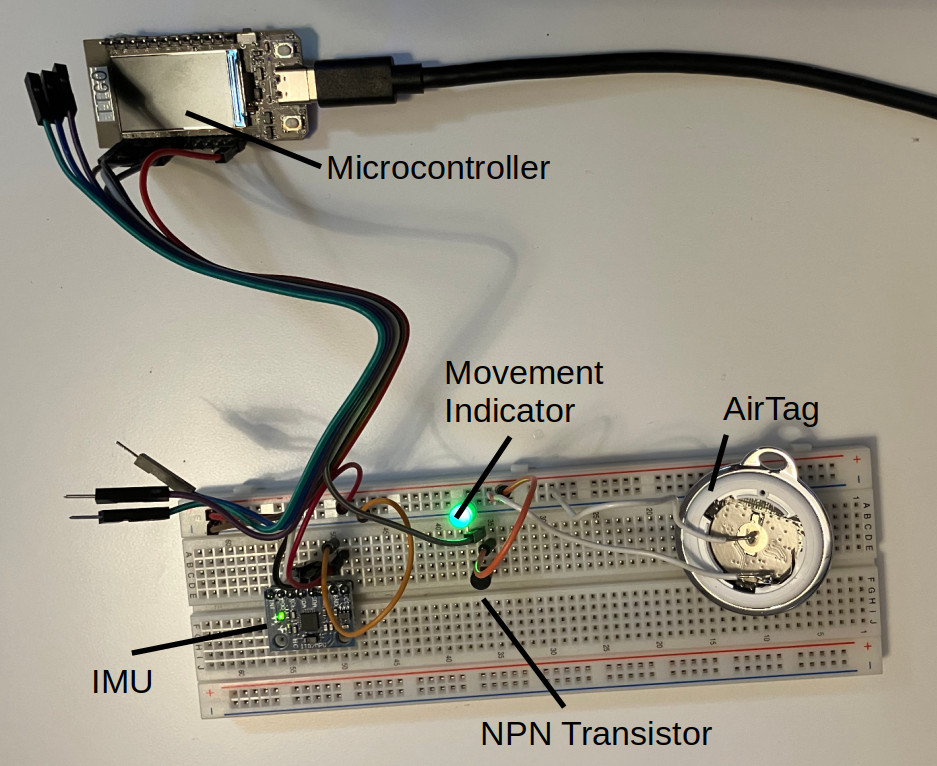
With the circuit, I demonstrated how I could selectively power an AirTag based on motion detection. In the following video, you can see how when I move the breadboard, the LED lights up, and the AirTag emits its power up chirp.
YouTube Link: AirTag - only broadcasts when movement is detected
However, I’m sad to report, I somehow damaged the AirTag when I soldered on the leads. After my modifications, I could no longer find the AirTag with Find My - even when I used a real CR2032 cell. Although I still haven’t taken this PoC to full completion, and I used a clone AirTag, I’m confident it could be made to work - a genuine Apple AirTag could be modified in this manner to make it harder to detect.
The source code used for this demo is a small alteration of Adafruit’s MPU6050 motion detection example.
Update 2025/05/15: Someone has commercialized an AirTag power cycling / broadcast cycling device. They are just cycling based on time, not using an IMU/motion sensor. See Undetectag.
